03-5117-2780
アクセス
お知らせ
NEWS

IBCコラムのご紹介
COLUMN
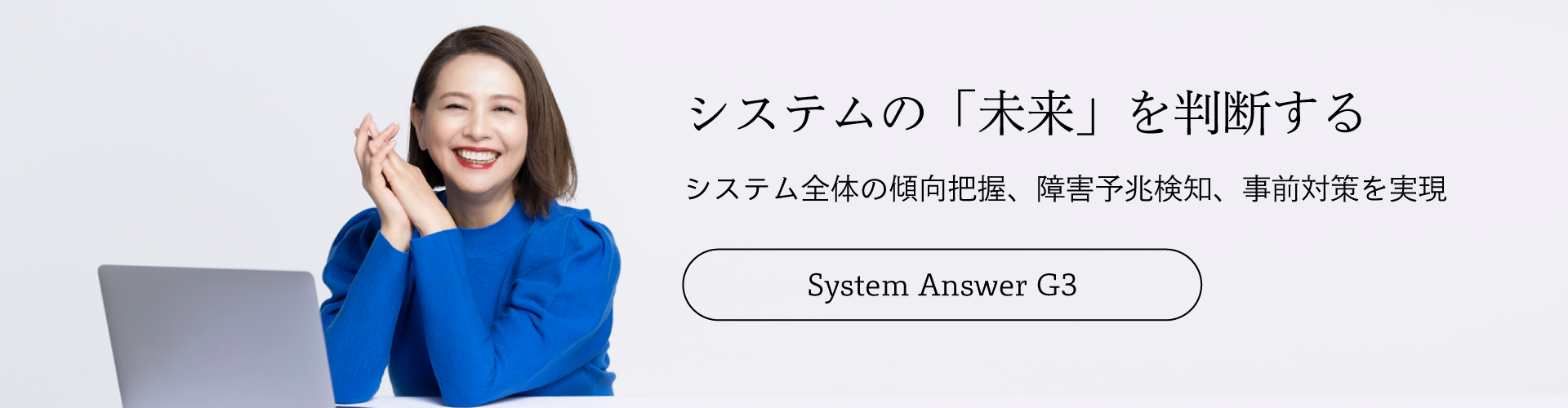
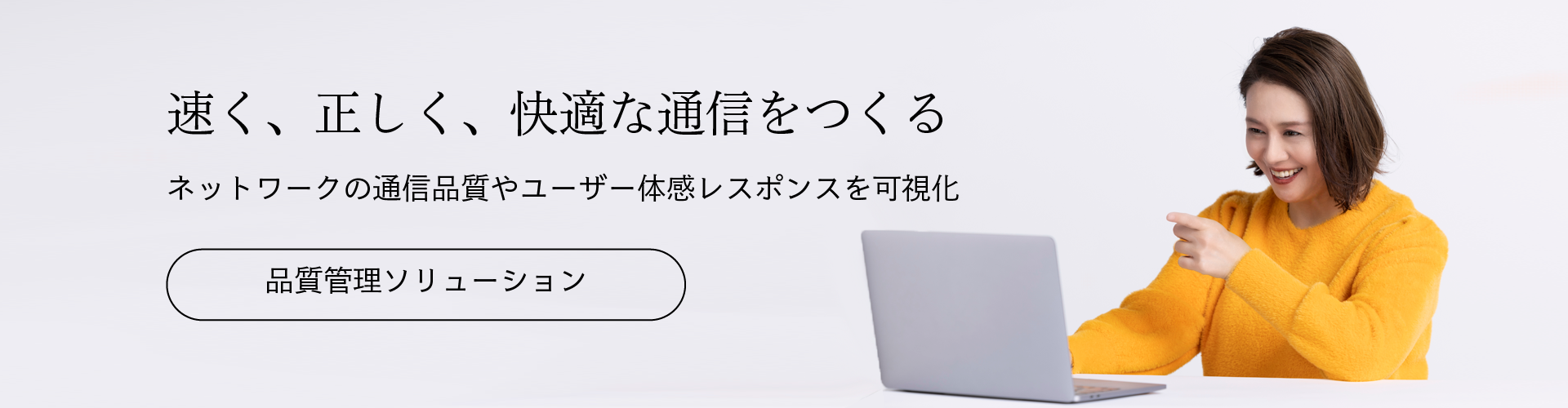
性能監視 / 情報管理、クラウド、セキュリティ、品質管理などにまつわる、今、IBC 社員がお客様に伝えたい想いを綴った連載コラムです。
事業内容
BUSINESS
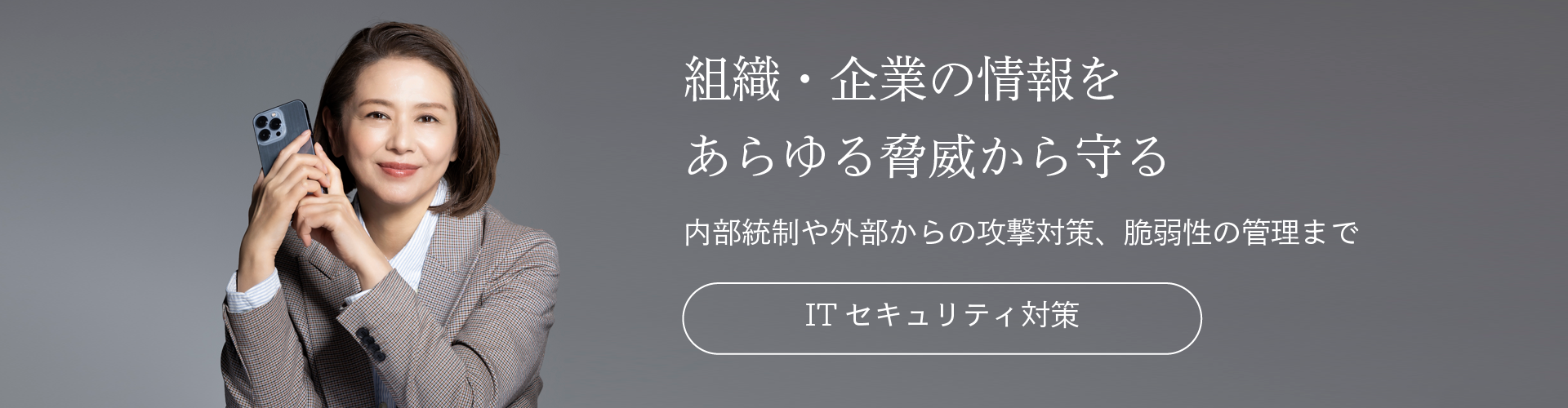
システム情報管理 / 性能監視ツール System Answer シリーズ の開発/販売/サポートから、ITシステムのコンサルティング、性能評価、設計・構築、IoT セキュリティ基盤サービスの開発/提供など、IT障害をゼロにするためのご支援をいたします。
アイビーシー株式会社について
ABOUT US

会社概要
Corporate Profile
アイビーシー株式会社の会社概要

代表挨拶
代表取締役社長 加藤裕之からのご挨拶

採用情報
Employment Information
中途・新卒採用情報

CSRへの取り組み
CSR
IBCは、 SDGsが目指す持続可能な社会の実現に貢献する企業であり続けるために、「世界を変えるための17の目標」への取り組みを進めています。
IR情報
IR INFORMATION
.png)